What is Infrastructure as Code and why you should care about it?
Infrastructure as Code (IaC) is an approach to managing and provisioning IT infrastructure through the use of machine-readable definition files, rather than manual hardware configuration or interactive configuration tools.
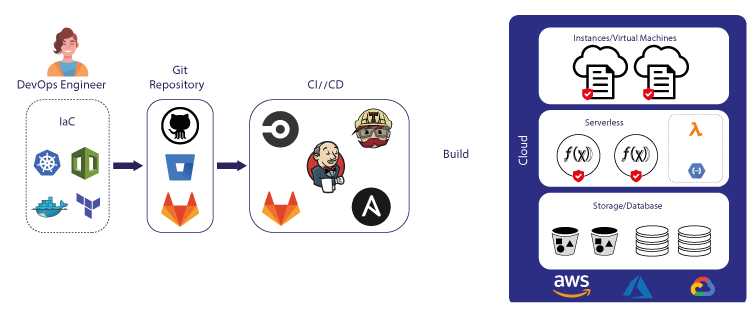
Introduction
Infrastructure as Code (IaC) is an approach to managing and provisioning IT infrastructure through the use of machine-readable definition files, rather than manual hardware configuration or interactive configuration tools. IaC treats infrastructure configuration in a manner similar to software development, enabling teams to manage and maintain infrastructure efficiently, predictably, and reliably.
IaC and Git
When Infrastructure as Code (IaC) is combined with Git, it significantly improves the auditability of your infrastructure. Auditability refers to the ability to track and verify changes, actions, and access to infrastructure over time, which is essential for security, compliance, and maintaining high-quality infrastructure management practices. Here are some ways in which IaC and Git together enhance auditability:
Version history
Git maintains a comprehensive version history of all changes made to the IaC files. Each commit in the Git repository includes information about who made the change, when the change was made, and a description of the change. This enables you to trace the evolution of your infrastructure and identify the root cause of any issues or discrepancies.
Accountability
Git's built-in user authentication and access control mechanisms ensure that only authorized team members can make changes to the infrastructure files. This helps to maintain individual accountability and provides a clear record of who is responsible for each change in the infrastructure configuration.
Traceability
By linking infrastructure changes to specific Git commits, you can establish traceability between the state of your infrastructure and the corresponding code. This makes it easier to correlate issues in the infrastructure with specific changes, helping to identify and resolve problems more quickly.
Code review and collaboration
Git's pull request mechanism facilitates a culture of code review and collaboration around infrastructure changes. This not only ensures that changes are thoroughly vetted before being merged but also provides an audit trail of the review process, including comments, approvals, and rejections.
Rollback and recovery
Git's ability to revert to previous versions of the infrastructure configuration helps maintain auditability in case of issues or failures. By rolling back to a known good state, you can quickly recover from problems while preserving a complete record of the actions taken to resolve the issue.
Automated testing and validation
By integrating IaC with Git, you can incorporate infrastructure changes into Continuous Integration/Continuous Deployment (CI/CD) pipelines. This allows for automated testing and validation of infrastructure changes before they are deployed, ensuring that they meet the necessary requirements and adhere to organizational policies. The results of these tests and validations are recorded, providing an additional layer of auditability.
Documentation
Storing IaC files in a Git repository serves as living documentation for the infrastructure, making it easier to track changes over time and understand how the infrastructure has evolved. This documentation can be used as evidence during audits to demonstrate compliance with various regulations and standards.
IaC Tools
Although there are so many IaC tools in the market, so far at 8grams, we only recommend 2 IaC tools: Terraform and Ansible. Terraform and Ansible are two of the most popular Infrastructure as Code (IaC) tools, and they serve different purposes within the IaC landscape. While Terraform is primarily focused on provisioning and managing infrastructure resources, Ansible is more focused on configuration management and application deployment.
In the context of being vendor-agnostic, both Terraform and Ansible are designed to work across multiple platforms and environments, providing flexibility and preventing vendor lock-in. Their ability to support various cloud providers, on-premises environments, and other services enables users to choose the best solutions for their needs without being tied to a specific vendor.
Terraform
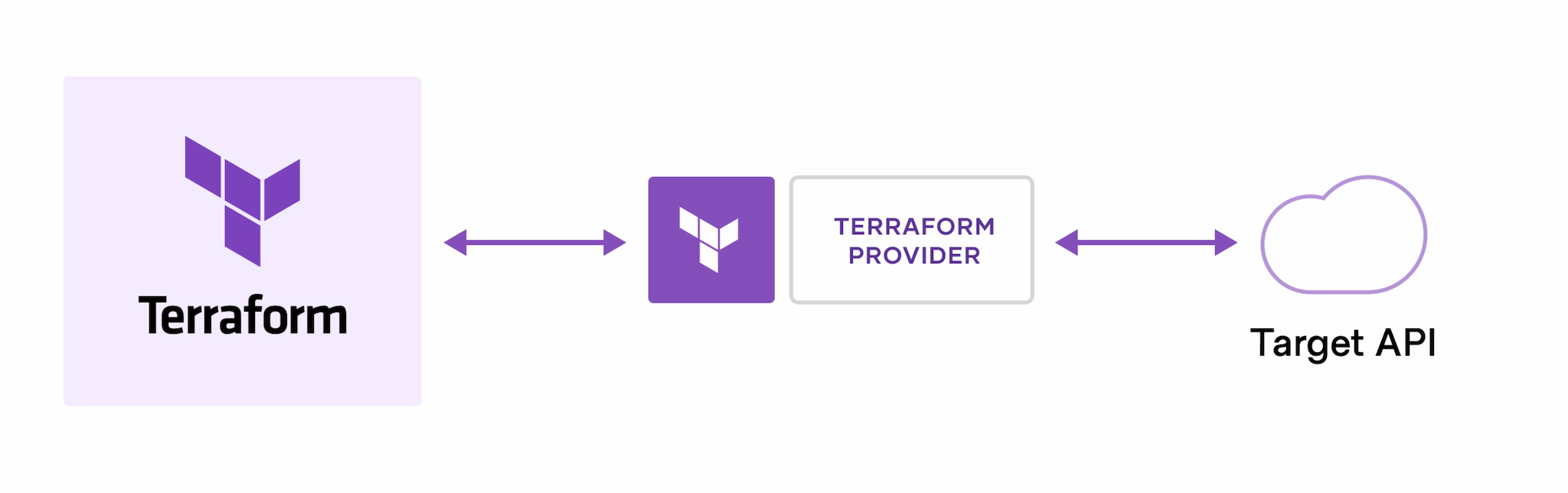
Terraform is an open-source IaC tool created by HashiCorp, designed to provision and manage infrastructure resources across multiple cloud providers and on-premises environments. Terraform uses a declarative language called HashiCorp Configuration Language (HCL) to define the desired state of infrastructure resources. The key features of Terraform include:
- Declarative language: Terraform's HCL allows you to define the desired end state of your infrastructure without specifying the detailed steps to achieve that state. This simplifies the configuration and makes it more readable and maintainable.
- Provider support: Terraform has an extensive ecosystem of providers, which are plugins that enable it to interact with various cloud platforms, on-premises environments, and other services. This allows you to manage resources across multiple platforms using a consistent workflow and syntax.
Terraform's vendor-agnostic approach is achieved through its provider system. Providers are plugins that allow Terraform to interact with various cloud platforms, on-premises environments, and other services. HashiCorp and the open-source community maintain a wide range of providers, supporting popular cloud platforms like AWS, Azure, Google Cloud, and many others, as well as on-premises solutions like VMware and OpenStack.
This extensive provider support allows Terraform to manage resources across multiple platforms using a consistent workflow and syntax. Users can easily switch between vendors or adopt a multi-cloud strategy without having to learn new tools or workflows. Additionally, since Terraform's configuration language (HCL) is declarative, the syntax remains consistent across providers, making it easier to adapt to different environments. - Modularity: Terraform promotes the use of modules, which are reusable, self-contained units of infrastructure configuration. Modules can be shared across projects and teams, improving consistency and reducing duplication of effort.
- State management: Terraform maintains a state file that keeps track of the current state of the infrastructure. This enables it to calculate the necessary changes to transition from the current state to the desired state defined in the configuration files.
- Plan & apply workflow: Terraform provides a two-step workflow, where you first generate a plan that shows the changes to be made, and then apply the plan to execute those changes. This allows you to review and approve changes before they are applied to the infrastructure.
Ansible

Ansible is an open-source automation tool used for configuration management, application deployment, and task automation. It uses a simple, human-readable language called YAML (Yet Another Markup Language) for defining infrastructure configuration. Ansible operates on an agentless architecture, relying on SSH (Secure Shell) or WinRM (Windows Remote Management) for connecting to remote systems. Key features of Ansible include:
- Playbooks: Ansible's configuration and deployment workflows are defined in playbooks, which are YAML files that describe the desired state of the system and the tasks required to achieve that state.
- Idempotency: Ansible's tasks are designed to be idempotent, meaning that they produce the same outcome regardless of how many times they are executed. This ensures that the system remains in the desired state, even if the playbook is run multiple times.
- Agentless architecture: Unlike some other configuration management tools, Ansible does not require the installation of an agent on the target systems. This simplifies deployment and reduces potential security risks.
- Inventory management: Ansible uses an inventory system to keep track of the target systems it needs to manage. The inventory can be static (defined in a file) or dynamic (generated from an external source, such as a cloud provider).
- Roles: Ansible supports the use of roles, which are reusable, modular units of configuration that can be shared across playbooks and projects. Roles promote reusability, consistency, and separation of concerns.
About 8grams
We are a small DevOps Consulting Firm that has a mission to empower businesses with modern DevOps practices and technologies, enabling them to achieve digital transformation, improve efficiency, and drive growth.
Ready to transform your IT Operations and Software Development processes? Let's join forces and create innovative solutions that drive your business forward.
Subscribe to our newsletter for cutting-edge DevOps practices, tips, and insights delivered straight to your inbox!
