Harbor: Install Open Source Container Registry on Kubernetes
Harbor is an open-source container registry that helps developers and organizations store, manage, and distribute container images and Helm charts.

Introduction
Harbor is an open-source container registry that helps developers and organizations store, manage, and distribute container images and Helm charts. It was designed with the goal of enhancing the security, scalability, and management of containerized applications in both small and large-scale environments. Harbor supports both Docker images and Helm charts, making it versatile for use with a variety of container orchestrators, such as Kubernetes.
At its core, Harbor provides an advanced registry platform with features like role-based access control (RBAC), image vulnerability scanning, and replication capabilities, all of which are essential for maintaining secure and scalable container ecosystems. Unlike other container registries, Harbor supports advanced functionalities like multi-tenancy, which allows organizations to create separate projects within the same Harbor instance. This provides users with more control over the accessibility and organization of their container images and Helm charts.
One of the most distinguishing aspects of Harbor is its seamless integration with container orchestration systems like Kubernetes, which is a must-have for modern cloud-native applications. Harbor not only acts as a private registry for storing images but also offers features that go beyond basic storage, making it a full-fledged solution for container image management, security, and distribution.
Background
Harbor was initially developed by VMware as an internal project to address the company's need for a secure, private container registry. With the rapid adoption of Docker and Kubernetes, VMware saw an opportunity to contribute to the growing container ecosystem by building a robust, scalable, and secure container registry solution.
Recognizing the potential impact of Harbor in the containerization space, VMware decided to release the project as open-source in 2017, and it quickly gained traction within the broader community. Harbor’s open-source nature allowed it to benefit from contributions from a wide range of developers, further enhancing its functionality and security.
In 2018, Harbor became an official project within the Cloud Native Computing Foundation (CNCF), the organization responsible for managing other popular cloud-native projects like Kubernetes and Prometheus. The CNCF’s endorsement helped Harbor gain even more visibility in the container ecosystem, and it is now considered one of the leading solutions for container image management.

Over the years, Harbor has continued to evolve, with regular updates that introduce new features and improve security. Its growing adoption is a testament to its ability to meet the needs of both small startups and large enterprises.
The Problem Harbor Solves
In the early stages of containerization, developers relied on public registries like Docker Hub to store and share container images. While these public registries worked well for small-scale applications, they posed several challenges for enterprise environments. Some of the most pressing issues that Harbor addresses include:
- Security Concerns: One of the primary challenges with using public registries is the security of container images. With an increasing number of vulnerabilities discovered in container images over time, organizations require a more secure platform that can detect and mitigate these risks. Harbor integrates with security tools like Trivy to scan images for known vulnerabilities, ensuring that only secure and trusted images are deployed in production environments.
- Scalability and Multi-Tenancy: Public registries often lack the ability to scale efficiently for large organizations. They also don’t provide a straightforward way to manage images across different teams or departments. Harbor offers a multi-tenant architecture, where users can define multiple projects within a single Harbor instance. Each project can have its own set of permissions, access policies, and security configurations, allowing organizations to manage container images in a more structured and scalable way.
- Compliance and Auditing: Many industries require compliance with security standards and regulatory requirements. Harbor provides logging and auditing capabilities, which help track and monitor the usage of images. These logs are essential for compliance and auditing purposes, ensuring organizations can meet security standards and regulations.
- Image Replication: Harbor supports image replication across multiple registries. This feature allows organizations to replicate images between different Harbor instances, whether on-premises or in the cloud. This is particularly useful for disaster recovery, high availability, or for organizations that operate in multiple geographical regions.
Architecture
The architecture of Harbor is designed for scalability, security, and high availability. It consists of several core components that work together to provide a seamless container image management experience. Understanding these components can help users leverage Harbor effectively in their environments.
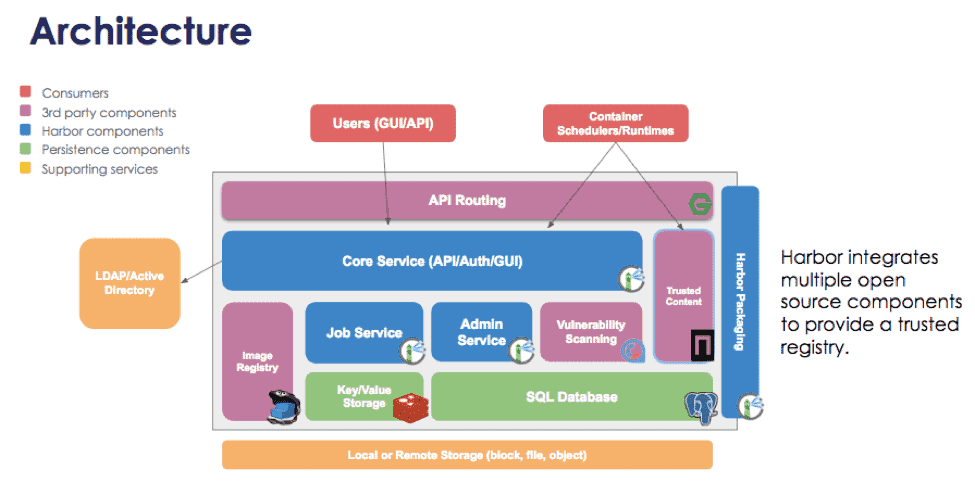
Core Service
At the heart of Harbor is the Core Service, which is responsible for managing and orchestrating the interactions between various components. It provides APIs that allow users to push, pull, and manage container images. The Core Service also handles user authentication, role-based access control, and other management tasks.
Registry
The Registry is the component where images are stored. It is based on the open-source Docker distribution, which allows Harbor to support Docker images and Helm charts. The Registry is designed for scalability and efficiency, enabling Harbor to handle large volumes of images.
Database
Harbor uses a relational database (such as PostgreSQL) to store metadata about container images, user access control policies, and other system settings. The database is essential for Harbor's ability to manage multiple projects and provide fine-grained access control.

Job Service
The Job Service is responsible for managing background tasks, such as vulnerability scanning, image replication, and garbage collection. It ensures that long-running processes do not block other operations, improving the overall performance of the system.
UI and API
Harbor provides both a web-based user interface (UI) and a RESTful API for interacting with the system. The UI is intuitive and easy to use, allowing developers and administrators to manage container images, configure security settings, and monitor system performance. The API is designed for programmatic access, allowing automation and integration with other tools.
Replication and Distribution
One of Harbor’s standout features is its ability to replicate images between different Harbor instances. This is achieved through the Replication Service, which allows users to replicate images to other registries, ensuring high availability, disaster recovery, and global distribution.
Security Integration in Harbor
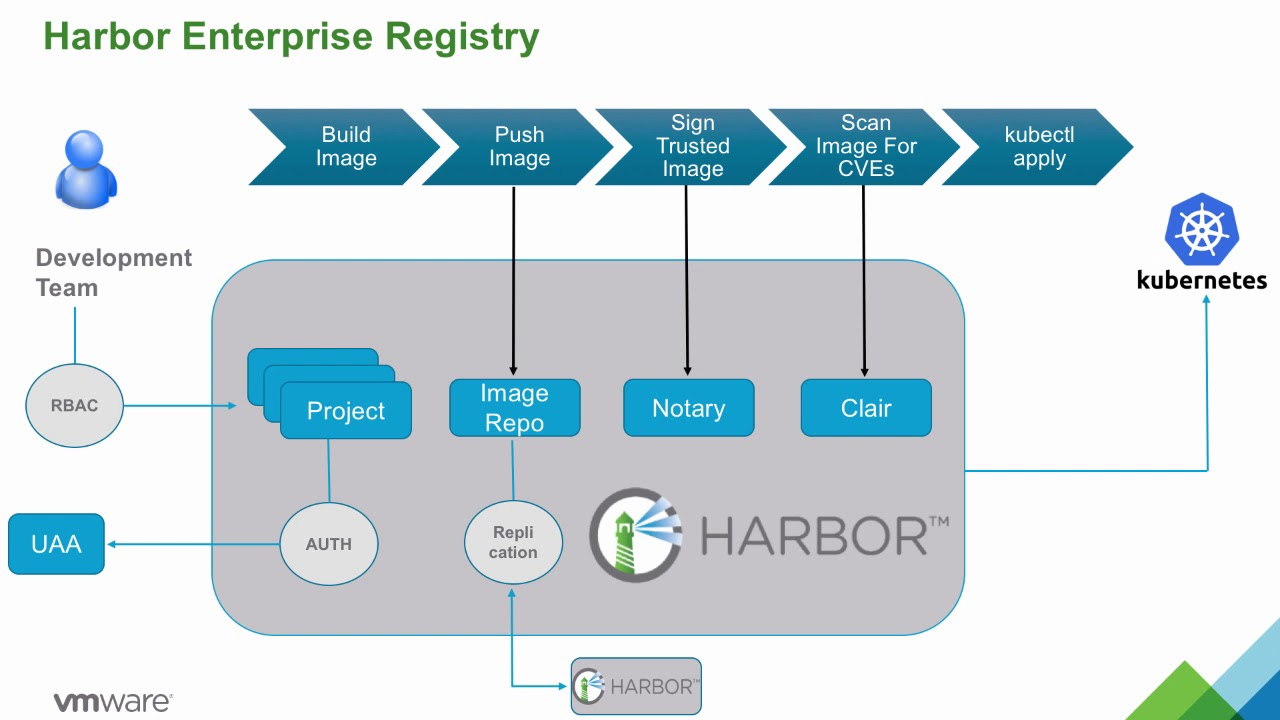
As containerized applications become an integral part of modern development pipelines, ensuring the security of these applications is paramount. Harbor excels in this area by integrating a variety of security mechanisms, enabling users to better protect their container images from vulnerabilities and threats. Harbor’s security features are designed to provide a comprehensive approach to container image management, addressing both vulnerabilities within the images themselves and the access control mechanisms surrounding them.
One of the standout security features in Harbor is its integration with Trivy, an open-source vulnerability scanner that checks container images for known security issues. Trivy scans images for a range of vulnerabilities, including CVEs (Common Vulnerabilities and Exposures) in the operating system packages, application dependencies, and configurations. When an image is pushed to Harbor, it is automatically scanned for vulnerabilities, and the results are presented to the user via the Harbor UI or API. This integration ensures that no image is deployed without first being thoroughly checked for security flaws, significantly reducing the risk of vulnerabilities being introduced into the production environment.
In addition to image scanning, Harbor provides role-based access control (RBAC), which allows administrators to define granular access policies for users and teams within the registry. With RBAC, organizations can enforce strict controls over who can upload, download, or modify images. For example, administrators can ensure that only trusted developers have the ability to push new images to the registry, while other users may only have read-only access to the images. This level of control minimizes the risk of unauthorized or accidental modifications to container images, enhancing the security posture of the entire registry.
Harbor also supports signed images, leveraging Notary to ensure that images are authentic and have not been tampered with. Image signing helps verify the integrity and authenticity of the images being pulled from the registry, adding an extra layer of security when deploying containers to production environments. This is especially important in scenarios where containers are being deployed across multiple clusters or cloud environments, ensuring that only verified images are used.
Moreover, Harbor offers audit logging, allowing administrators to track every action performed within the registry. This includes information on who pushed an image, who pulled it, and who modified access control policies. Having detailed logs helps organizations maintain compliance with security standards and ensures transparency in the actions taken within the registry.
By combining features like vulnerability scanning, RBAC, image signing, and audit logging, Harbor provides a robust and secure container registry solution that helps enterprises manage their container images with confidence, knowing that both the images and the access controls are constantly monitored and protected.
Harbor vs Other Container Registries
In the container ecosystem, several container registries compete with Harbor, each offering its own set of features and advantages. Among the most notable alternatives are GitLab Container Registry, GitHub Container Registry (GHCR), and Google Artifact Registry. While each of these registries provides the basic functionality of storing and managing container images, Harbor offers several unique advantages, particularly in terms of enterprise-level features and security.
| Feature | Harbor | GitLab Container Registry | GHCR (GitHub Container Registry) | Google Artifact Registry |
|---|---|---|---|---|
| Open Source | Yes | Yes | Yes | No |
| Security Features | Image scanning (Trivy integration), RBAC, Signatures | Vulnerability scanning (Snyk integration), RBAC | Image scanning (GitHub Advanced Security), RBAC | Image scanning, RBAC |
| Multi-tenancy Support | Yes | Yes (with Projects) | Yes (with Repositories) | Yes (with Repositories) |
| Replication Support | Yes | Yes (for GitLab CI/CD pipelines) | No (external tooling needed) | Yes |
| Helm Chart Support | Yes | No | No | No |
| Scalability | High (supports large enterprise environments) | Medium (suitable for smaller projects) | Medium (suitable for GitHub-centric workflows) | High (designed for enterprise-level needs) |
| CI/CD Integration | Seamless integration with Kubernetes and CI/CD pipelines | Native integration with GitLab CI/CD | Native integration with GitHub Actions | Native integration with Google Cloud CI/CD |
| Private Repository Support | Yes | Yes | Yes | Yes |
| Cloud Vendor Lock-in | No (works on any cloud or on-prem) | No (works on any cloud or on-prem) | Yes (best integrated with GitHub) | Yes (Google Cloud) |
| Free Tier | Yes | Yes | Yes | No (free tier with limits) |
Install Harbor on Kubernetes
Harbor is designed for native deployment on Kubernetes and supports installation via Helm. Ensure that Helm is installed on your machine prior to proceeding with the installation.
Register Harbor's Helm Package
~$ helm repo add harbor https://helm.goharbor.ioHarbor needs PostgreSQL for its data persistent. For installing PostgreSQL, see this article below:

Harbor also needs Redis for cache, for example login session, registry manifest, and a queue for the jobservice. For installing Redis, see this article below

Install Harbor
Create a PVC for Harbor's Registry and Trivy.
Then, create a values to override Harbor's default Helm Values. Please adjust the values according to your needs.
Now we can install them:
~$ kubectl apply -f volume.yaml
~$ helm install harbor -f values.yaml harbor/harborNow we can access the Harbor's Dashboard via browser on https://registry.example.com and login with admin using password from harborAdminPassword


