Hadolint: Dockerfile Linter
To guarantee seamless, repeatable builds and production deployments, it is essential to write effective, safe, and maintainable Dockerfiles. Hadolint, a Dockerfile linter, is one tool that aids with this endeavor.
Introduction
By enabling developers to bundle apps and their dependencies into containers, Docker has completely changed the process of developing and deploying software. The Dockerfile, a script that specifies how the container is constructed, is the central component of any Docker container. To guarantee seamless, repeatable builds and production deployments, it is essential to write effective, safe, and maintainable Dockerfiles. Hadolint, a Dockerfile linter, is one tool that aids with this endeavor.
What is it?

An open-source linter called Hadolint was created to examine Dockerfiles and make sure best practices are followed. In this sense, linting is the process of checking code for any mistakes, inconsistencies, and standard violations prior to execution. Hadolint looks for problems with security, efficiency, maintainability, and Docker best practices when it comes to Dockerfiles.
Hadolint is a companion that assists developers in creating Dockerfiles that are safe, optimized, and compliant with industry standards; it is not a Docker build tool in and of itself. It is driven by a set of regulations that take into account both the community's cumulative knowledge and the most recent Docker guidelines.
How Does It Operate?
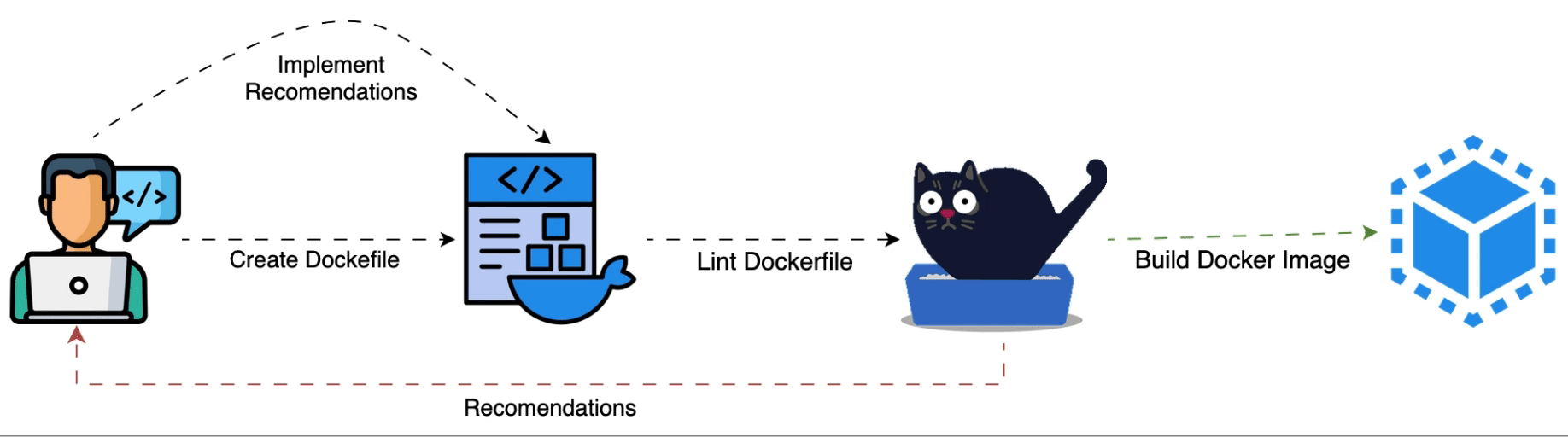
Hadolint works by examining a Dockerfile's contents and comparing them to a list of pre-established guidelines. These guidelines are intended to identify frequent errors, inefficiencies, and security flaws. Hadolint might, for instance, highlight the use of out-of-date software versions, superfluous image layers, or `RUN` commands that could be streamlined.
Line by line, the linter parses the Dockerfile and looks for problems using static analysis and regular expressions. Depending on how serious the problem was, it then generates errors or warnings. Usually, each problem has an explanation and occasionally even a solution idea.
Because Hadolint is so adaptable, users can turn on or off particular rules based on the requirements of their projects. Additionally, it facilitates the creation of custom rules, which can be very helpful in specialized development environments or huge organizations.
Key Hadolint Features
Hadolint is a useful tool for Dockerfile linting because it has a number of strong capabilities.
Comprehensive Rules
A vast array of Dockerfile best practices are covered by the extensive set of rules that come with Hadolint. The official Dockerfile best practices documentation, security recommendations, and performance optimization methods serve as the foundation for these regulations. They assist developers in avoiding typical errors, increasing the effectiveness of picture construction, and lowering the possibility of security flaws.
Personalized Guidelines
Although Hadolint offers a set of default rules, developers can alter them as they see fit. Depending on the requirements of the project or the team's preferences, users can enable or disable particular rules. To enforce particular policies, such as making sure that a USER directive is always included in the Dockerfile or that all images use a particular base image, custom rules can also be created.
Integration of CI/CD
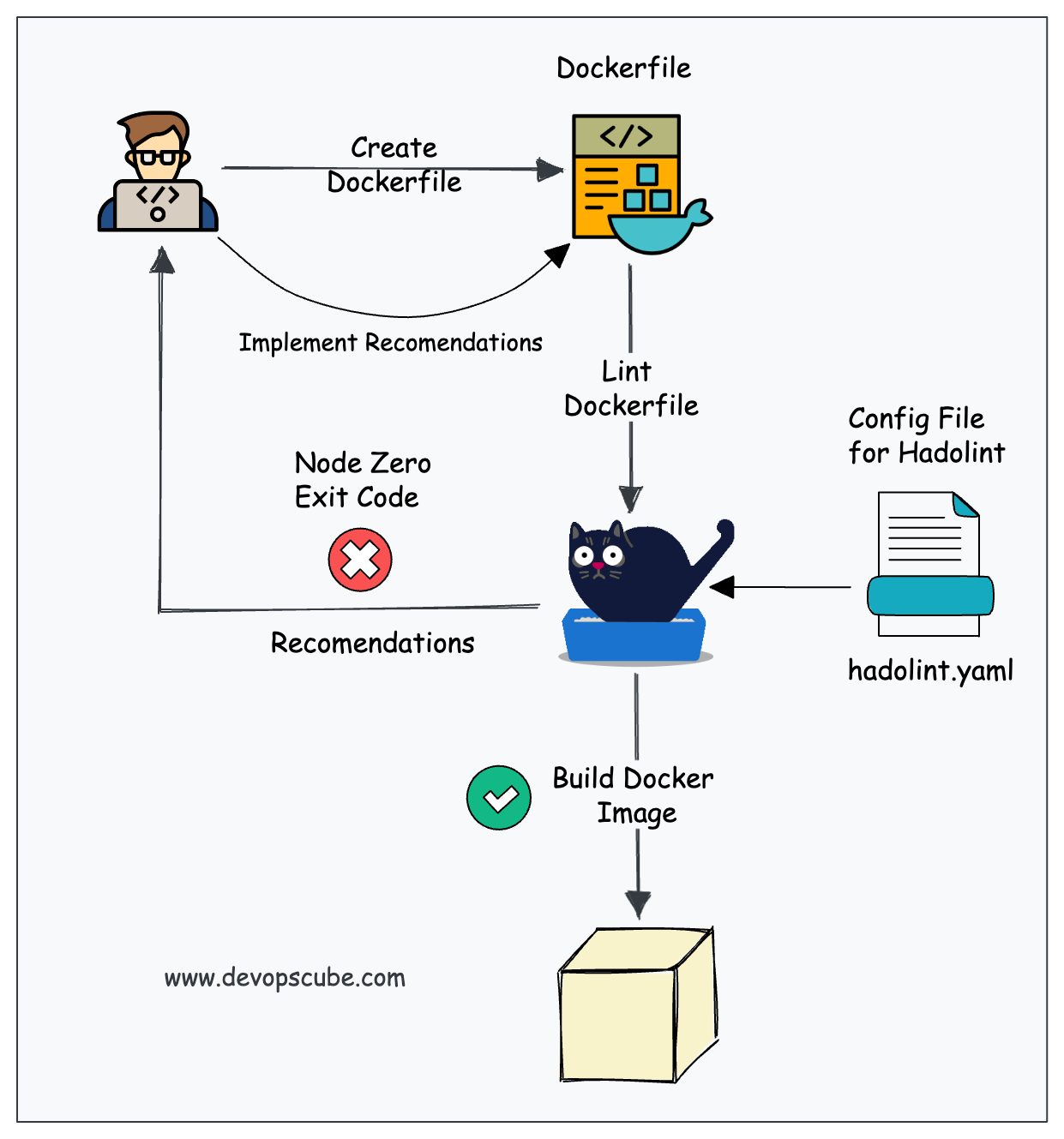
Hadolint's smooth integration with Continuous Integration and Continuous Deployment (CI/CD) pipelines is one of its main advantages. Developers may automatically lint Dockerfiles on each commit or pull request by incorporating Hadolint into CI/CD workflows. Before going into production, this guarantees that any modifications made to the Dockerfile follow best practices and are error-free.
It is simple to combine Hadolint with well-known CI/CD platforms like Jenkins, CircleCI, GitLab CI, and GitHub Actions. By identifying problems early in the development cycle, this enhances the quality of the code and lowers the possibility of adding errors or inefficiencies to the container image.
Integration of the IDE
Editors such as Visual Studio Code (VS Code), which allows plugins for real-time linting, can be combined with Hadolint for developers who prefer to work in a combined Development Environment (IDE). This integration makes it simpler to adhere to best practices and prevent errors by giving developers immediate feedback while they create or edit Dockerfiles.
Community-driven and open-source
Since Hadolint is an open-source project, contributions from the worldwide community are beneficial to it. This gives developers the chance to add new guidelines, bug fixes, and enhancements in addition to guaranteeing that the tool is updated frequently to match the most recent Docker best practices. Innovation is encouraged and the tool will adapt to the demands of the Docker ecosystem thanks to this community-driven approach.
Advantages of Hadolint
For developers working with Dockerfiles, Hadolint provides a number of benefits, particularly in large teams or companies where efficiency, security, and consistency are critical.
Better Consistency and Quality of Code
All Dockerfiles adhere to uniform best practices thanks to Hadolint. In large teams, where several developers could be working on the same codebase, this is very crucial. Teams may make sure that Dockerfiles are written consistently and in an understandable manner by utilizing Hadolint. It lessens the possibility of causing minor problems that may result from discrepancies between several Dockerfiles.
Improved Protection
Dockerfiles are not an exception to the rule that security is a major concern in contemporary software development. Malicious actors may be able to take advantage of vulnerabilities introduced by a poorly prepared Dockerfile. Potential security threats that Hadolint can assist in identifying include:
- Using base images that are out-of-date or unsafe
- Unnecessarily executing processes as the root user
- Sensitive data, including credentials or secrets, could be exposed in the Dockerfile.
Hadolint assists developers in creating more secure Docker images by identifying these problems early.
Efficiency and Performance
Because Docker images are constructed in layers, the final image size increases with the number of layers. Hadolint can spot inefficiencies in Dockerfiles that result in extra layers and bigger image sizes, including duplicate `RUN` commands or poorly optimized build processes. Developers can create Dockerfiles that generate smaller, more effective images by heeding Hadolint's advice. This can lead to quicker build times and less storage expenses.
Quicker Cycle of Development
Early in the development cycle, Hadolint assists in identifying mistakes and problems. Developers may automatically lint Dockerfiles with each modification by incorporating it into CI/CD pipelines. This minimizes the amount of effort needed debugging later on by guaranteeing that any problems are found and fixed before they reach production. Early feedback allows developers to fix possible problems while the context is still new, which further lessens cognitive burden.
Promotes the Use of Best Practices
Clean, maintainable, and safe build processes are equally as important as functionality when it comes to Dockerfiles. Hadolint pushes developers to adhere to best practices that they might otherwise ignore. This entails selecting the appropriate base images, appropriately handling dependencies, cache optimization, and, when necessary, choosing COPY over ADD. Better long-term maintainability and scalability result from adhering to these guidelines.
Restrictions and Points to Remember
Hadolint is an effective tool, but it is not perfect, and not all of its recommendations will work in every situation. Each suggestion should be carefully considered by developers in light of their particular use case. Here are some important things to think about:
Not Every Suggestion Is Useful Every Time
Large Dockerfile commands should be divided into smaller, more detailed steps, according to Hadolint. For instance, it might suggest breaking up a RUN instruction's several commands into separate ones. Because each RUN command creates a new layer, this can result in larger Docker images even if it can aid with readability and consistency.
However, in some situations, especially when optimizing for image size, combining commands into a single RUN phrase may be a superior option. For instance, reducing the number of layers in the final image by consolidating package installations into a single RUN command can result in reduced image files and possibly faster builds. In this instance, Hadolint's recommendation to divide instructions for readability may clash with performance improvement.
Context Is Important
Although each Dockerfile has a distinct context, Hadolint's principles are founded on common best practices. Based on variables including picture size, build performance, and security requirements, developers should consider the benefits and drawbacks of adhering to specific recommendations. For instance, Hadolint may indicate that a root user is being used in the Dockerfile, but in certain situations, executing as root throughout the build process may be required for particular tasks (such installing system dependencies).
Customization of Rules and False Positives
Hadolint may provide false positives, or alerts for problems that aren't actually troublesome in the context of a particular project, just like any other static analysis tool. Thankfully, Hadolint lets users modify the linting rules, so they can turn off specific tests or adjust the linter's behavior to better fit their requirements.
