Getting Started with Security Lifecycle Management
Security lifecycle management is the practice of securing and protecting digital assets through a structured, ongoing process.

Introduction
In today’s increasingly digital world, security is no longer an afterthought but a foundational aspect of any system, organization, or network. From securing personal data to protecting enterprise networks, managing security risks throughout a system's lifecycle is crucial. This is where security lifecycle management (SLM) comes in.
Security lifecycle management is the practice of securing and protecting digital assets through a structured, ongoing process. It consists of several phases, each aimed at addressing different vulnerabilities and risks. At its core, SLM is designed to protect sensitive data, monitor the environment for vulnerabilities, and ensure that access is restricted based on a need-to-know basis. This process ensures that security is continually maintained, with a focus on preventing, detecting, and responding to threats.
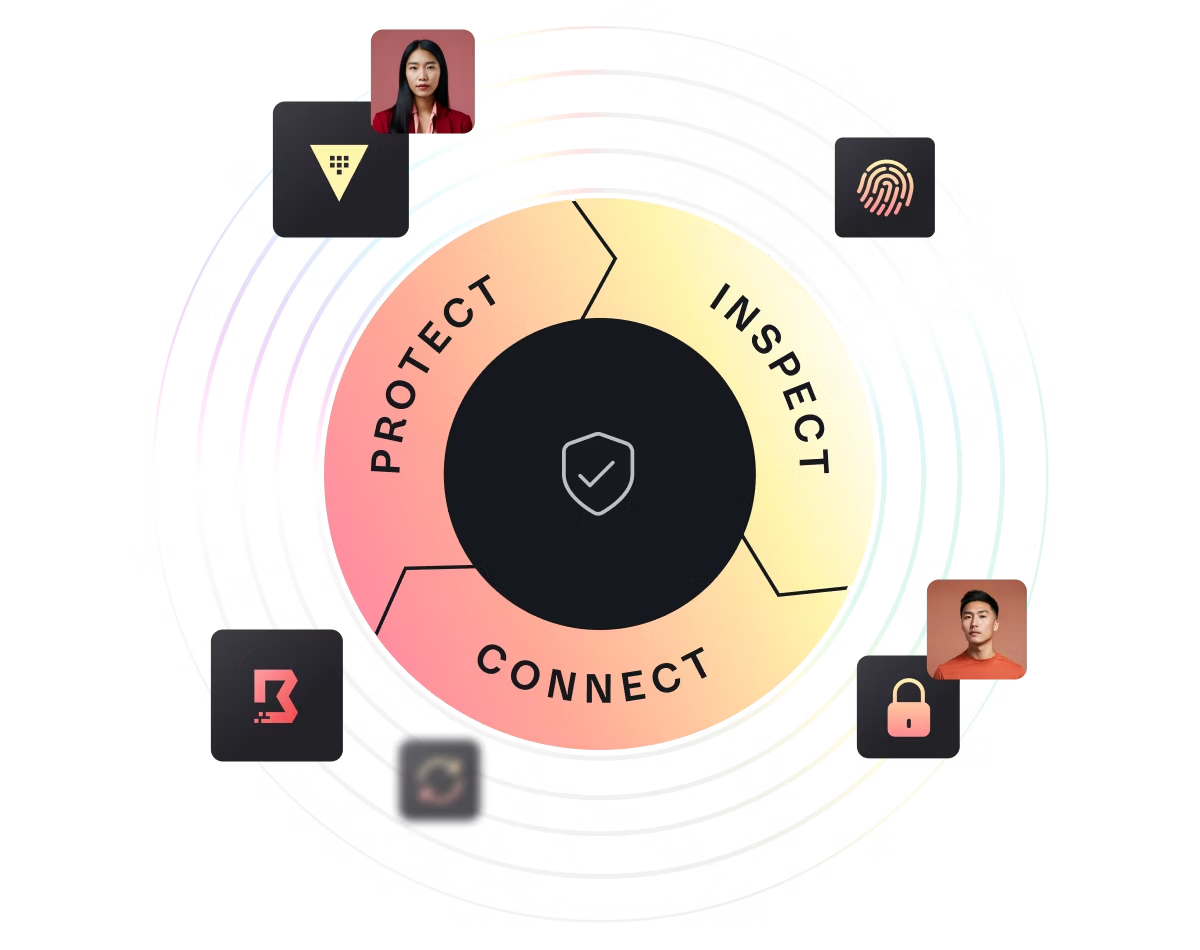
The lifecycle is generally divided into three primary phases: Protect, Inspect, and Connect. Each of these phases is vital for building a robust security framework. This article will explore each of these phases in detail and provide guidance on how to implement them using open-source, vendor-agnostic tools.
Protect: Guarding Sensitive Data Across All Environments
Protecting sensitive data is arguably the most critical element in any cybersecurity strategy. Sensitive data can range from personal information like Social Security numbers and bank details to intellectual property, trade secrets, and internal company communications. Exposing such data can lead to severe consequences, including financial loss, reputational damage, legal repercussions, and loss of customer trust.
In the modern IT landscape, data exists across multiple environments—on-premises, in the cloud, and in hybrid systems. This diversity in storage and processing locations presents unique challenges for organizations, which need centralized solutions to safeguard data across all platforms.
Strategies for Data Protection
A robust data protection strategy starts with centralizing control over access and ensuring that sensitive data is not easily exposed. Centralized systems of record can help track and control data, minimizing the risk of accidental leaks or breaches.
Encryption is also a crucial component of data protection. When data is encrypted, it becomes unreadable to anyone who doesn’t have the correct decryption key, ensuring its confidentiality even if it is intercepted. Alongside encryption, strong authentication mechanisms, such as multi-factor authentication (MFA), are essential for ensuring that only authorized users can access the data.
Tools
One popular tool is Vault by HashiCorp, an open-source solution that provides centralized management of sensitive data such as passwords, API keys, and certificates. Vault offers features like encryption-as-a-service, fine-grained access control, and detailed audit logs, making it ideal for hybrid cloud environments. For those using Amazon Web Services (AWS), AWS Secrets Manager is a fully managed service that securely stores and automatically rotates secrets like passwords and API keys. It integrates seamlessly with AWS services and uses AWS Key Management Service (KMS) for encryption, while tracking access through AWS CloudTrail.
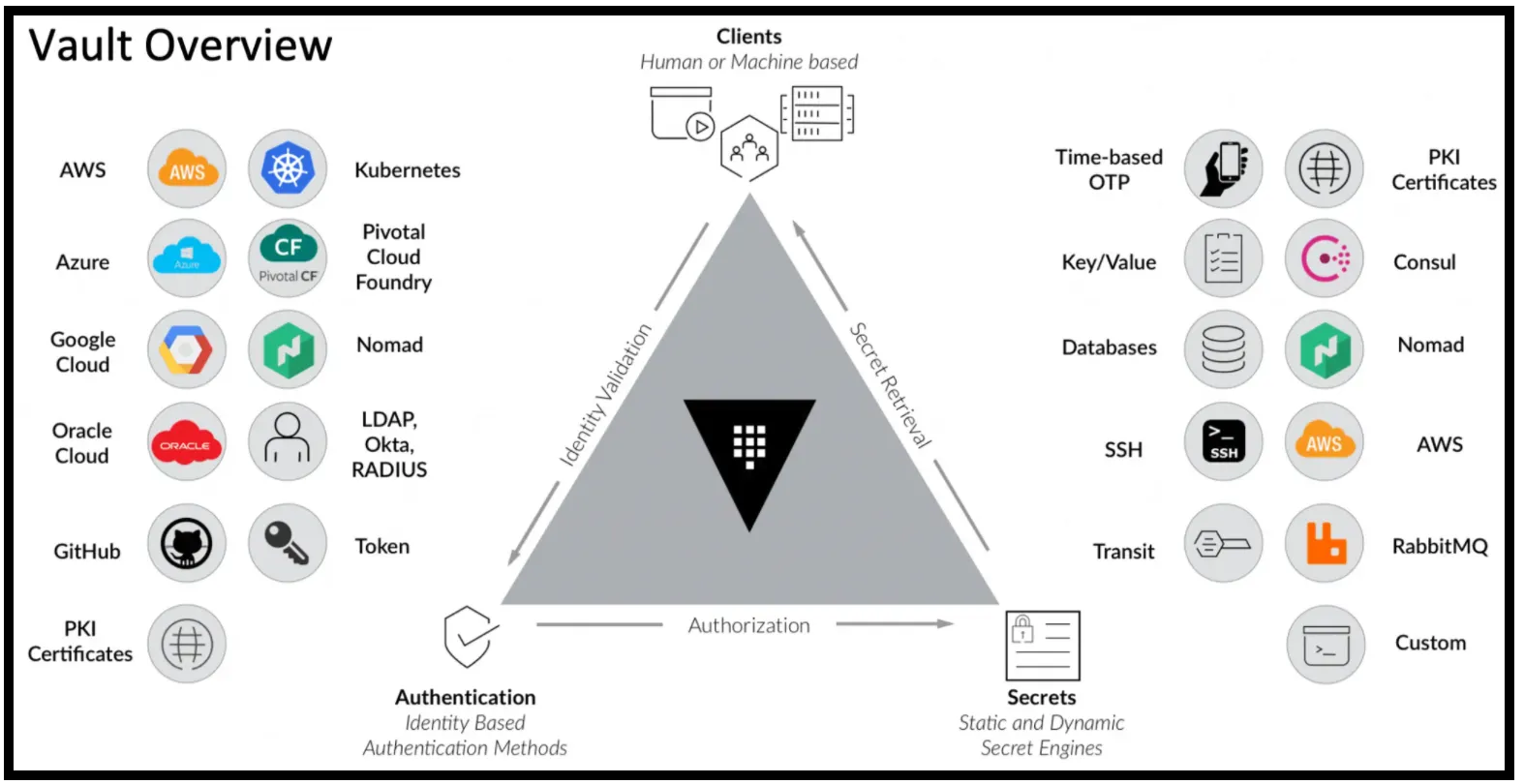
For organizations using Google Cloud, GCP Key Management Service (KMS) is a centralized solution for managing encryption keys. GCP KMS leverages Hardware Security Modules (HSMs) to protect keys and integrates with other Google Cloud services. Lastly, Azure Key Vault offers a similar set of features for organizations on Microsoft Azure. It allows for secure management of secrets and cryptographic keys, integrates with Azure Active Directory (AAD) for access control, and provides audit logging through Azure Monitor.
Inspect: Continuously Scanning for Unsecured Sensitive Data
Once sensitive data is protected, it’s crucial to continuously monitor the environment to identify potential vulnerabilities. Cyber threats evolve rapidly, and what was secure yesterday may be vulnerable today. Regular inspection of the environment ensures that new risks are detected early and mitigated before they can be exploited.
The process of inspection involves scanning systems for unsecured sensitive data, monitoring for unauthorized access, and identifying any misconfigurations that could expose critical resources. A proactive, continuous inspection approach is essential for maintaining an effective security posture and minimizing the risk of data breaches.
Strategies for Inspecting the Environment
To detect vulnerabilities and exposures, regular scans of the environment must be conducted. This includes scanning for exposed credentials, unsecured sensitive data, and other vulnerabilities that could be exploited by attackers. Systems should also be audited for misconfigurations, particularly with regard to cloud services, firewalls, and access controls.
Privileged Access Management (PAM) is another key strategy for inspection. PAM involves managing and monitoring the use of privileged accounts—those with elevated access rights to critical systems. Misuse of privileged accounts is a common attack vector, so monitoring and controlling access to these accounts is vital.
Tools
The Inspect phase focuses on identifying unsecured or exposed sensitive data within your environment. This requires continuous scanning for vulnerabilities in code, configurations, and access controls. Several tools can help automate this process to ensure security and compliance.
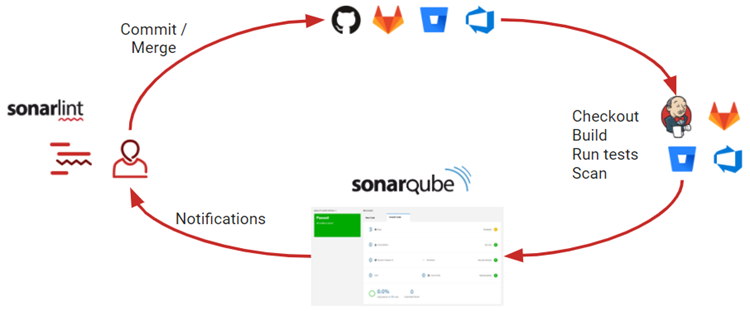
- SonarQube: a widely-used open-source tool for continuous inspection of code quality and security vulnerabilities. It supports multiple programming languages and detects issues like SQL injection and XSS, helping developers secure sensitive data during the development process.
- Checkmarx: a static application security testing (SAST) tool that identifies vulnerabilities in code, including risks related to sensitive data handling. It integrates with CI/CD pipelines to provide real-time security scanning throughout the development cycle.
- Snyk: focuses on identifying vulnerabilities in open-source dependencies and container security. It scans for issues in both the codebase and its dependencies, helping developers ensure that third-party libraries do not introduce vulnerabilities that could expose sensitive data.
- OWASP Dependency-Check: scans for vulnerabilities in third-party libraries and dependencies. It helps detect known security flaws that could lead to the exposure of sensitive data, especially in applications relying heavily on external code.
Connect: Enforcing Least-Privileged Access Based on Trusted Identities
One of the fundamental principles of cybersecurity is the Principle of Least Privilege (PoLP). This principle states that users should be granted the minimum level of access necessary to perform their duties. By enforcing least-privileged access, organizations can reduce the attack surface and limit the potential damage caused by compromised accounts or systems.
The idea is simple: if a user or system doesn’t need access to a particular resource, it shouldn’t have it. For example, an employee working in the finance department may not need access to HR systems, and a web developer doesn’t need unrestricted access to production servers. By restricting access based on the user’s role and job function, the organization minimizes the likelihood of unauthorized access or data leaks.
Strategies for Enforcing Least-Privileged Access
To enforce PoLP, organizations must first define roles and responsibilities clearly and ensure that access controls are aligned with these roles. This can be achieved through role-based access control (RBAC), where access rights are assigned based on the user’s role within the organization. This ensures that users only have access to the data and resources they need to do their job.
Another key strategy is adopting a Zero Trust architecture. Zero Trust assumes that no user, device, or network is inherently trustworthy. Every access request is treated as potentially malicious, and strict authentication and authorization procedures are enforced for every action. This is achieved by continuously verifying users and devices before granting them access to any system or resource.
Identity and device authentication are also crucial for ensuring that only trusted entities are allowed to connect to the network. By enforcing multi-factor authentication (MFA), organizations can ensure that even if credentials are compromised, unauthorized access will still be blocked.
Tools
Keycloak is an open-source identity and access management (IAM) solution that provides features like single sign-on (SSO), identity federation, and fine-grained access control. It supports protocols such as OAuth 2.0, OpenID Connect, and SAML 2.0, making it highly versatile for different environments. Keycloak allows organizations to centralize authentication and authorization, enforce strong access policies, and ensure secure user management across applications. It is particularly useful for companies that require centralized identity management for multiple applications.
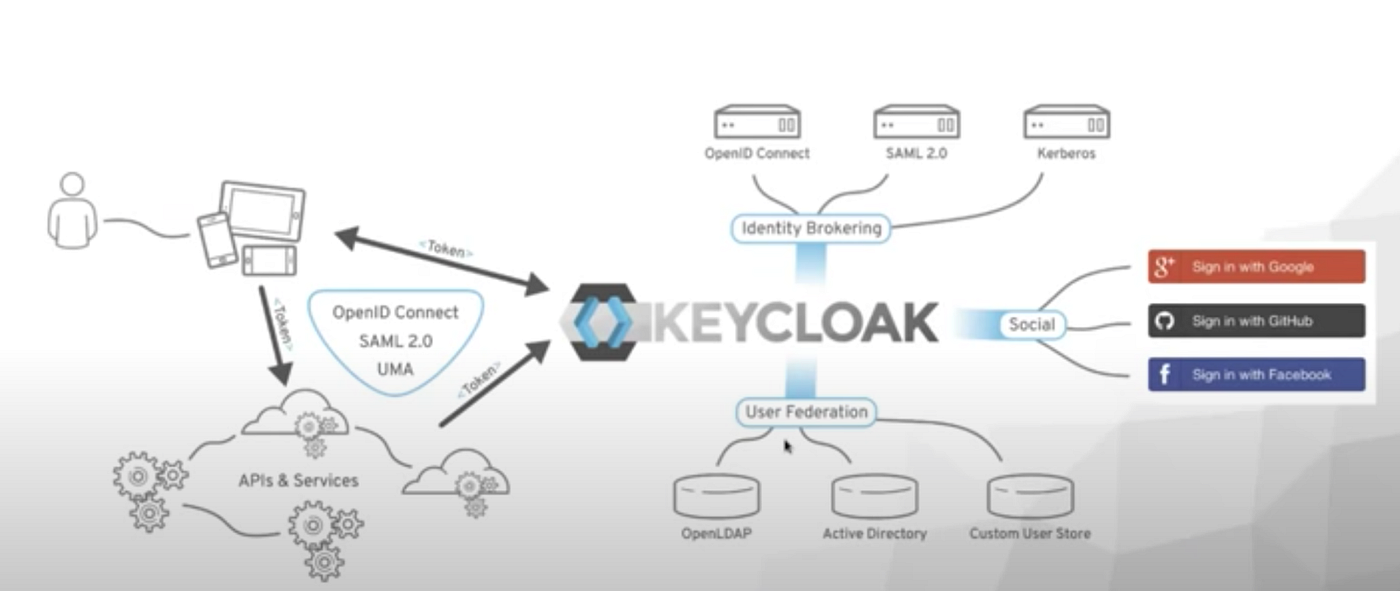
An alternative to Keycloak is Auth0, a cloud-based identity management service that offers secure authentication, authorization, and identity federation. It supports a wide range of authentication protocols and can integrate with various applications, enabling developers to implement secure login systems quickly. Auth0 provides features like multi-factor authentication (MFA) and social login, making it a scalable solution for enterprises seeking a vendor-agnostic, easy-to-implement identity management system.
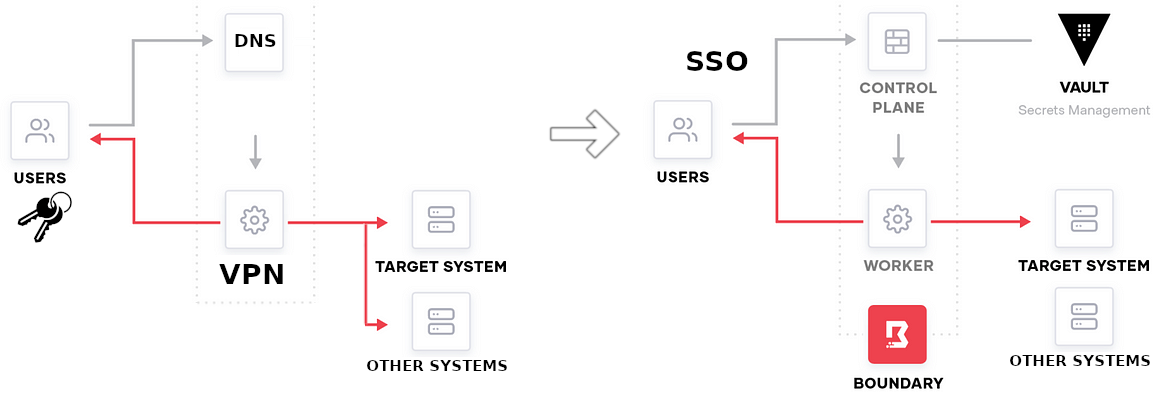
For managing secure access to applications and infrastructure, Boundary by HashiCorp is another powerful open-source solution. Boundary allows users to access systems without exposing credentials or requiring VPN access, providing a secure method of managing access to dynamic environments. It focuses on identity-based access, ensuring that users can only access the resources they are authorized for. Boundary also offers session management and auditing capabilities, which are essential for maintaining secure environments.
An alternative to Boundary is Teleport, an open-source access platform that allows secure access to infrastructure and applications. It supports SSH, Kubernetes, databases, and internal web apps, offering a unified way to manage and audit access. With its identity-aware proxy and support for multi-factor authentication, Teleport is a robust solution for managing secure, least-privileged access in cloud-native environments.
Building a Unified Security Ecosystem
While the Protect, Inspect, and Connect phases are often discussed separately, they must work together to create a holistic security posture. Integrating these phases ensures that security is continuously maintained and that potential threats are detected and mitigated before they can cause damage.
The Protect phase ensures that sensitive data is secured and that only authorized individuals can access it. The Inspect phase continuously scans the environment for potential vulnerabilities, ensuring that any unsecured data or misconfigurations are identified and addressed. Finally, the Connect phase enforces the principle of least privilege, ensuring that access is strictly controlled based on verified identities and roles.
By integrating these phases, organizations create a feedback loop that ensures security is not static but constantly evolving in response to emerging threats and changes in the environment. For instance, if a vulnerability is identified during the inspection phase, access controls in the Connect phase can be adjusted to mitigate any risk. Similarly, if data protection measures are found to be insufficient during an inspection, they can be strengthened through new encryption protocols or access policies.
